Tag Archives: cyberwar
The looming spectre of cyberwar with Russia
 In the world of cyber (as in security), the question of the week seems to be, "are we going to cyberwar with Russia?"
White House Press Secretary Josh Earnest thinks so. A week after President Obama singled out Russia as being responsible for cybera...
In the world of cyber (as in security), the question of the week seems to be, "are we going to cyberwar with Russia?"
White House Press Secretary Josh Earnest thinks so. A week after President Obama singled out Russia as being responsible for cybera...
Alex Gibney on Stuxnet and why we need to talk about cyberwar
 It's been six years since we've discovered Stuxnet, the worm that infected Windows PCs worldwide, and was eventually traced to the US and Israel as a way to attack Iran's nuclear program. It was the first time a cyberweapon was used to attack a physi...
It's been six years since we've discovered Stuxnet, the worm that infected Windows PCs worldwide, and was eventually traced to the US and Israel as a way to attack Iran's nuclear program. It was the first time a cyberweapon was used to attack a physi...
MIT’s digital lookout in the crows nest of cyber warfare
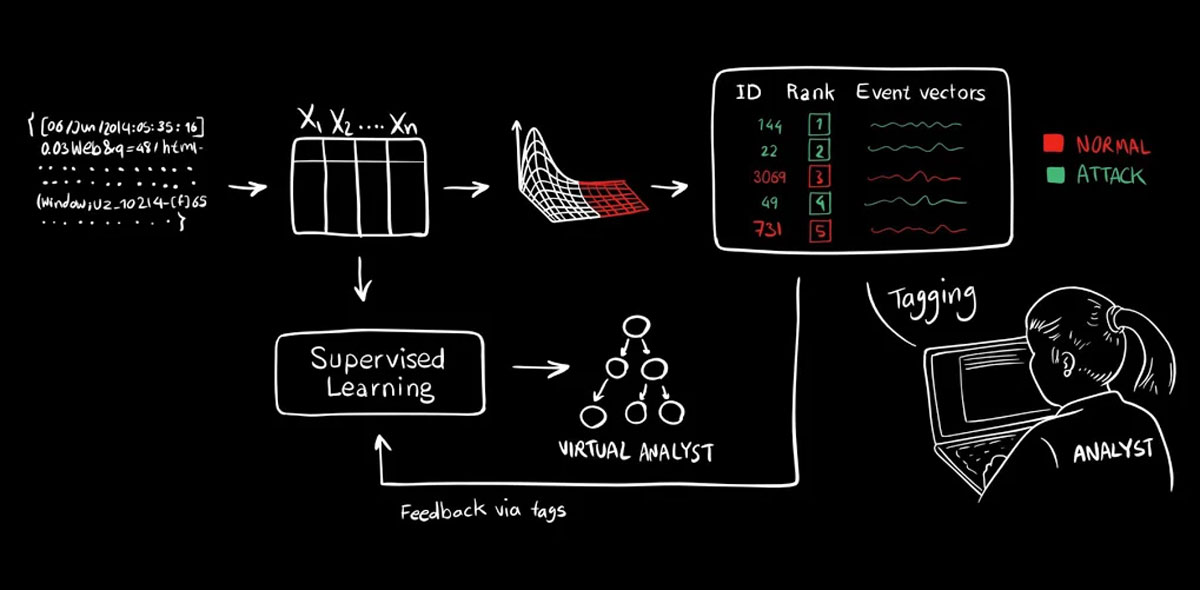 "Think about the system as a virtual analyst," says Kaylan Veermachaneni, co-creator of MIT's latest artificial intelligence. He's a research scientist at the university's Computer Science and Artificial Intelligence lab that, along with Ignacio Arna...
"Think about the system as a virtual analyst," says Kaylan Veermachaneni, co-creator of MIT's latest artificial intelligence. He's a research scientist at the university's Computer Science and Artificial Intelligence lab that, along with Ignacio Arna...
Report: ISIS’s Twitter propaganda efforts have stalled
 The Islamic State isn't having much luck recruiting new members online these days. Twitter suspended 125,000 accounts sympathetic to the jihadist organization between June and October of last year and it appears to be making an impact, according to a...
The Islamic State isn't having much luck recruiting new members online these days. Twitter suspended 125,000 accounts sympathetic to the jihadist organization between June and October of last year and it appears to be making an impact, according to a...
Report: ISIS’s Twitter propaganda efforts have stalled
 The Islamic State isn't having much luck recruiting new members online these days. Twitter suspended 125,000 accounts sympathetic to the jihadist organization between June and October of last year and it appears to be making an impact, according to a...
The Islamic State isn't having much luck recruiting new members online these days. Twitter suspended 125,000 accounts sympathetic to the jihadist organization between June and October of last year and it appears to be making an impact, according to a...
Report: ISIS’s Twitter propaganda efforts have stalled
 The Islamic State isn't having much luck recruiting new members online these days. Twitter suspended 125,000 accounts sympathetic to the jihadist organization between June and October of last year and it appears to be making an impact, according to a...
The Islamic State isn't having much luck recruiting new members online these days. Twitter suspended 125,000 accounts sympathetic to the jihadist organization between June and October of last year and it appears to be making an impact, according to a...
Tallinn Manual defines the legal groundwork for cyberwarfare
The advent of cyberwarfare raises any number of legal quandaries, let alone ethical ones: when it's possible to do serious damage without crossing a border or firing a shot, where do you stop? NATO's Cooperative Cyber Defence Centre of Excellence (CCDCOE) is publishing the finished version of a non-binding guide, the Tallinn Manual, that could settle at least the legal disputes. For the most part, it demands a measured, one-for-one response and attempts to minimize collateral damage. Digital retaliation is appropriate if the state is a victim of a hacking attack, but bombs and guns should only come into play if virtual combat leads to real casualties. Any attacks should likewise steer clear of civilians, and simply having the capacity or desire for a hacking campaign doesn't make someone a target -- there has to be an "imminent" threat to justify a preemptive strike. NATO isn't formally adopting the Tallinn Manual as policy, and it's difficult to know whether the organization's member nations (or any other country) would honor the guidelines when parties on all sides have been pushing the boundaries of cyberwarfare for years. Still, we'll have to start somewhere if we want to draw a line in the silicon.
[Image credit: US Army, Flickr]
Via: TechWeek Europe
Source: CCDCOE
China claims its defense sites face constant US hacking attacks
China is routinely accused of launching concerted hacking campaigns against the US, many of them reportedly tied directly to the army's Unit 61398 in Shanghai. If you believe the Ministry of Defense's spokesman Geng Yansheng, however, just the opposite is true. Along with claiming that China would never hurt (or rather, hack) a fly, he asserts that the Ministry and China Military Online sites faced an average of 144,000 hacking attempts per month from foreign sources in 2012, 62.9 percent of which allegedly came from the US. The Ministry's man stops short of leveling cyberwarfare charges, although he notes the US' recent plans to expand and formally define its cyberwar strategy. There's some 'splainin to do, he argues. While there isn't a formal US response, we suspect that neither side is an innocent dove here -- China is just the most recent to cry foul.
Filed under: Internet
Via: Reuters
Kaspersky Labs preps its own OS to guard vital industry against cyberwarfare
Kaspersky Labs' namesake Eugene Kaspersky is worried that widely distributed and potentially state-sponsored malware like Flame and Stuxnet pose dire threats to often lightly protected infrastructure like communication and power plants -- whatever your nationality, it's clearly bad for the civilian population of a given country to suffer even collateral damage from cyberattacks. To minimize future chaos and literally keep the trains running, Kaspersky and his company are expanding their ambitions beyond mere antivirus software to build their own, extra-secure operating system just for large-scale industry. The platform depends on a custom, minimalist core that refuses to run any software that isn't baked in and has no code outside of its main purposes: there'll be no water supply shutdowns after the night watch plays Solitaire from an infected drive. Any information shared from one of these systems should be completely trustworthy, Kaspersky says. He doesn't have details as to when the OS will reach behind-the-scenes hardware, but he stresses that this is definitely not an open-source project: some parts of the OS will always remain confidential to keep ne'er-do-well terrorists (and governments) from undermining the technology we often take for granted.
Filed under: Software
Kaspersky Labs preps its own OS to guard vital industry against cyberwarfare originally appeared on Engadget on Tue, 16 Oct 2012 13:28:00 EDT. Please see our terms for use of feeds.
Permalink The Next Web |
The Next Web |  Eugene Kaspersky, Securelist | Email this | Comments
Eugene Kaspersky, Securelist | Email this | Comments 

